- Posts: 3
- Thank you received: 1
Forum Login
How to hack a WiFi password?
Rendering Error in layout Widget/Social: Call to a member function exists() on null. Please enable debug mode for more information.
6 years 4 months ago #8898 by Dr.John
How to hack a WiFi password? was created by Dr.John
For the purpose of the demonstration, we were guilty of hacking... from our own access point. We proceeded in several stages.
Step 1: find the method
How to hack a WiFi password? To answer this question, we asked Google. The engine guided us to a complete tutorial. Under cover of presentation of the method to 'test your Wi-Fi network', this tutorial gives the complete procedure to 'crack' a Wep key.
Step 2: Prepare the material
A particular software suite (which we will not name) stands out for the security of Wi-Fi networks. But its Windows version is inefficient. The tutorial recommends using a Linux Live CD dedicated to security. We download from the site this version, then we engrave it. All drivers for WiFi cards are already provided on this CD, but not all WiFi cards are compatible for hacking. Hack a WiFi password is not so easy. However, a list of compatible cards is indicated, in which is the USB card that we use, an SMC model.
Step 3: put the Wi-Fi card in the right mode
We put the freshly burned CD in the drive and restart the computer. Linux is loading. All devices are recognized, and the interface is close to that of Windows. Operations will, however, take place by launching the necessary programs in text mode in windows called 'console', the Linux equivalent of the Windows DOS command window. In a first console window, two lines of commands are enough to pass the Wi-Fi USB card in so-called 'monitor' mode. This will simulate activity on Wi-Fi access points and speed up hacking.
Step 4: See available networks
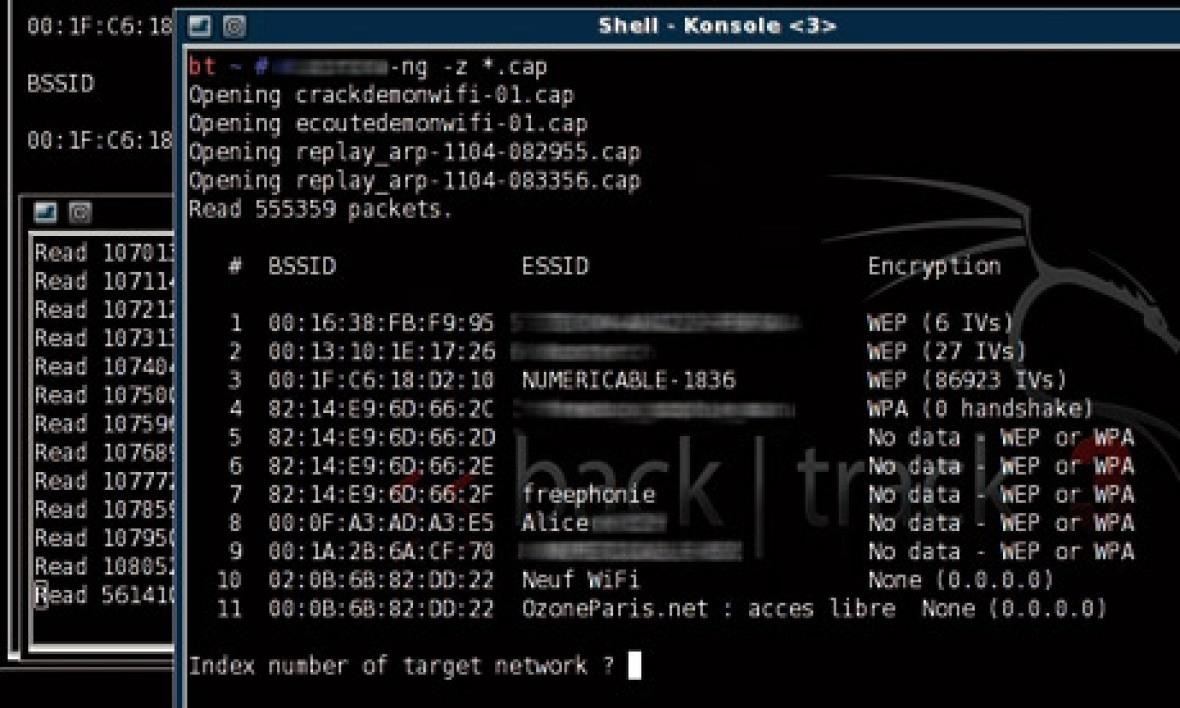
The security suite used for our hacking includes three separate utilities. In a console, we launch the first utility giving it a series of parameters that tells it what to do: display all available networks nearby and keep all the data of this 'listening' in a file. The program displays the very large number of available networks with a certain amount of information, the BSSID or Mac address of the access point, the Essid, the Datas (data) transiting the network as well as the type of protection used. Many Wep networks are detected, regardless of the service provider, often recognizable by the name of the network itself.
Step 5: Listen to the access point to hack
We then restart the program by targeting our access point. For this, we give as parameter the BSSID of the access point. The list of access points, and computers that are connected to it, is displayed again. To 'crack' the Wep key, it is the data in transit that will be recorded by the program. As there is no PC connected to the access point, there is no data that passes... This is a problem for us.
Step 6: stimulate and simulate activity
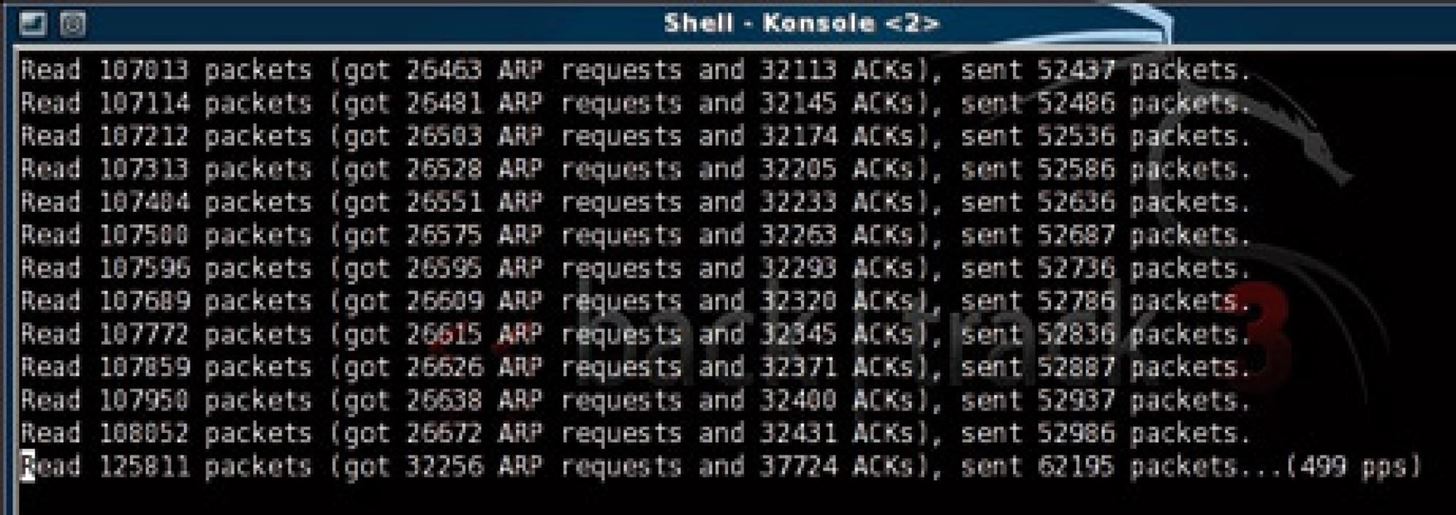
We run in parallel the second utility giving it as a parameter the name of the network, the Mac address of the WiFi access point and that of our WiFi card. We carry out a 'false authentication' attack, which goes force the access point to be 'chatty' with our Wi-Fi card. In the window of the first program, the data column is racing: we have obtained more than 90,000 'packets' of data. According to the tutorial, 40,000 would have been enough.
Step 7: find the right key
As the listening continues, we launch the third utility of the suite, which is responsible for calculating the key.
For this, we enter the name of the file in which the first program saves the data. A list of access points will be displayed. We choose ours and... the calculation of the key Wep is, in our case, instantaneous!
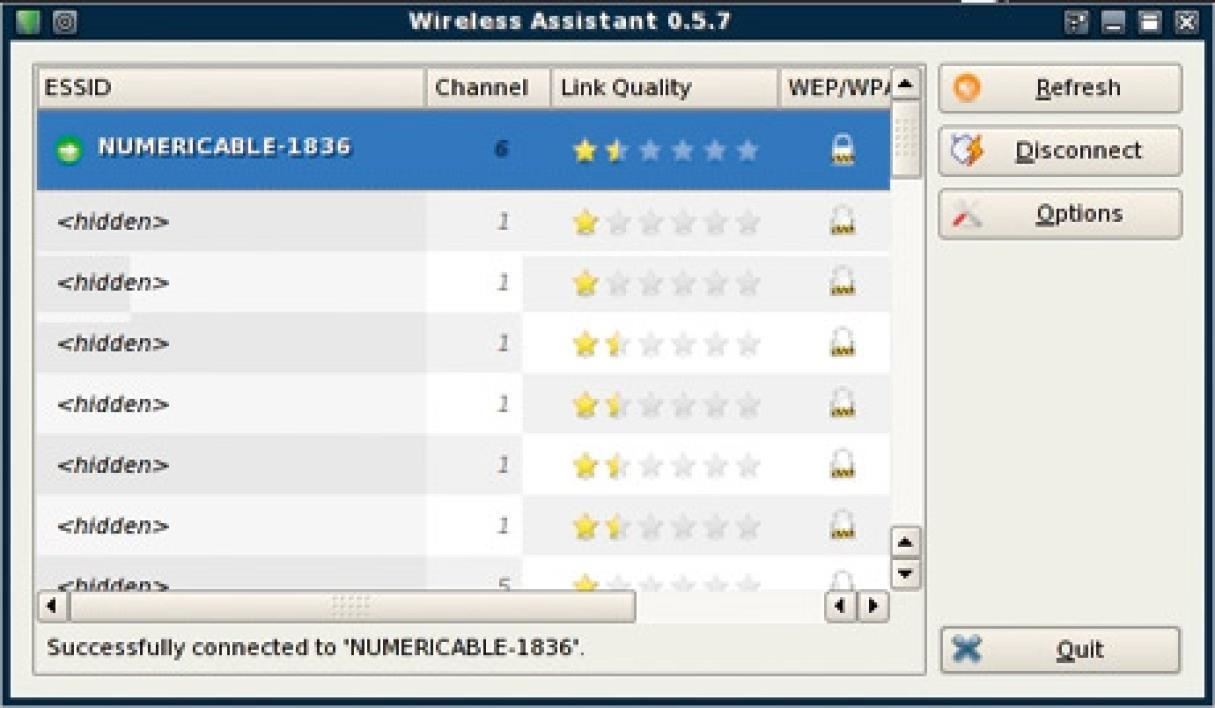
Step 8: Test the key
We are launching the Linux Wireless Connection Wizard. Then, we select our access point in the list. We then ask to connect to it. The Wep key is then requested. We enter the key we just calculated.
Total success!
WiFi password is hacked
Step 1: find the method
How to hack a WiFi password? To answer this question, we asked Google. The engine guided us to a complete tutorial. Under cover of presentation of the method to 'test your Wi-Fi network', this tutorial gives the complete procedure to 'crack' a Wep key.
Step 2: Prepare the material
A particular software suite (which we will not name) stands out for the security of Wi-Fi networks. But its Windows version is inefficient. The tutorial recommends using a Linux Live CD dedicated to security. We download from the site this version, then we engrave it. All drivers for WiFi cards are already provided on this CD, but not all WiFi cards are compatible for hacking. Hack a WiFi password is not so easy. However, a list of compatible cards is indicated, in which is the USB card that we use, an SMC model.
Step 3: put the Wi-Fi card in the right mode
We put the freshly burned CD in the drive and restart the computer. Linux is loading. All devices are recognized, and the interface is close to that of Windows. Operations will, however, take place by launching the necessary programs in text mode in windows called 'console', the Linux equivalent of the Windows DOS command window. In a first console window, two lines of commands are enough to pass the Wi-Fi USB card in so-called 'monitor' mode. This will simulate activity on Wi-Fi access points and speed up hacking.
Step 4: See available networks
The security suite used for our hacking includes three separate utilities. In a console, we launch the first utility giving it a series of parameters that tells it what to do: display all available networks nearby and keep all the data of this 'listening' in a file. The program displays the very large number of available networks with a certain amount of information, the BSSID or Mac address of the access point, the Essid, the Datas (data) transiting the network as well as the type of protection used. Many Wep networks are detected, regardless of the service provider, often recognizable by the name of the network itself.
Step 5: Listen to the access point to hack
We then restart the program by targeting our access point. For this, we give as parameter the BSSID of the access point. The list of access points, and computers that are connected to it, is displayed again. To 'crack' the Wep key, it is the data in transit that will be recorded by the program. As there is no PC connected to the access point, there is no data that passes... This is a problem for us.
Step 6: stimulate and simulate activity
We run in parallel the second utility giving it as a parameter the name of the network, the Mac address of the WiFi access point and that of our WiFi card. We carry out a 'false authentication' attack, which goes force the access point to be 'chatty' with our Wi-Fi card. In the window of the first program, the data column is racing: we have obtained more than 90,000 'packets' of data. According to the tutorial, 40,000 would have been enough.
Step 7: find the right key
As the listening continues, we launch the third utility of the suite, which is responsible for calculating the key.
For this, we enter the name of the file in which the first program saves the data. A list of access points will be displayed. We choose ours and... the calculation of the key Wep is, in our case, instantaneous!
Step 8: Test the key
We are launching the Linux Wireless Connection Wizard. Then, we select our access point in the list. We then ask to connect to it. The Wep key is then requested. We enter the key we just calculated.
Total success!
WiFi password is hacked
Please Log in or Create an account to join the conversation.
Who's Online
We have 260 guests and no members online
N00BZ
- ljamal
- ljamal74
- mikeg2atest
- ducchinhbui
- anjarezt
Cookies
EU e-Privacy Directive
This website uses cookies to manage authentication, navigation, and other functions. By using our website, you agree that we can place these types of cookies on your device.
You have declined cookies. This decision can be reversed.
You have allowed cookies to be placed on your computer. This decision can be reversed.